Understanding Virtual Private Cloud (VPC) Architecture: A Comprehensive Guide
Are you interested in exploring the world of Virtual Private Cloud (VPC) architecture? Look no further! In this comprehensive guide, we will delve into the intricacies of VPC architecture, providing you with a detailed understanding of its inner workings. Whether you are a seasoned IT professional or simply curious about the topic, this article aims to offer valuable insights that cater to all levels of expertise.
What is Virtual Private Cloud (VPC)?
In today’s digital landscape, businesses and organizations are increasingly relying on cloud computing to store and process data, run applications, and scale their operations. A Virtual Private Cloud (VPC) is a virtual network dedicated to a specific organization, providing them with the benefits of cloud computing while maintaining a secure and isolated environment.
Unlike traditional cloud computing models where resources are shared among multiple tenants, a VPC allows organizations to have their own private space within a cloud provider’s infrastructure. This means that they can define their own IP address range, create subnets, and configure network access control to meet their specific requirements.
VPCs offer a range of advantages, including enhanced security, scalability, and flexibility. By creating a VPC, organizations can ensure that their data and applications remain isolated from other tenants, reducing the risk of unauthorized access or data breaches. Additionally, VPCs allow organizations to scale their resources as needed, providing the ability to easily add or remove virtual machines, storage, and other services.
The Benefits of VPC Architecture
Let’s take a closer look at some of the key benefits of utilizing VPC architecture:
Enhanced Security
One of the primary advantages of VPC architecture is the enhanced security it provides. By having a dedicated virtual network, organizations can implement robust security measures to protect their data and applications. They can define network access control lists (ACLs) and security groups to control inbound and outbound traffic, ensuring that only authorized requests are allowed. Additionally, VPCs can be connected to on-premises networks using VPN or dedicated connections, further extending the security boundary.
Scalability and Flexibility
VPCs offer scalability and flexibility, allowing organizations to easily scale their resources as needed. With a few clicks, organizations can add or remove virtual machines, storage, and other services to meet their changing demands. This scalability ensures that businesses can rapidly respond to increased workloads or seasonal spikes without any disruption.
Cost Optimization
VPCs also enable cost optimization by allowing organizations to pay for only the resources they use. With the ability to scale resources up or down as needed, organizations can avoid overprovisioning and reduce unnecessary expenses. Additionally, VPCs offer options for cost-effective data transfer, allowing organizations to minimize their data transfer costs between VPCs and on-premises networks.
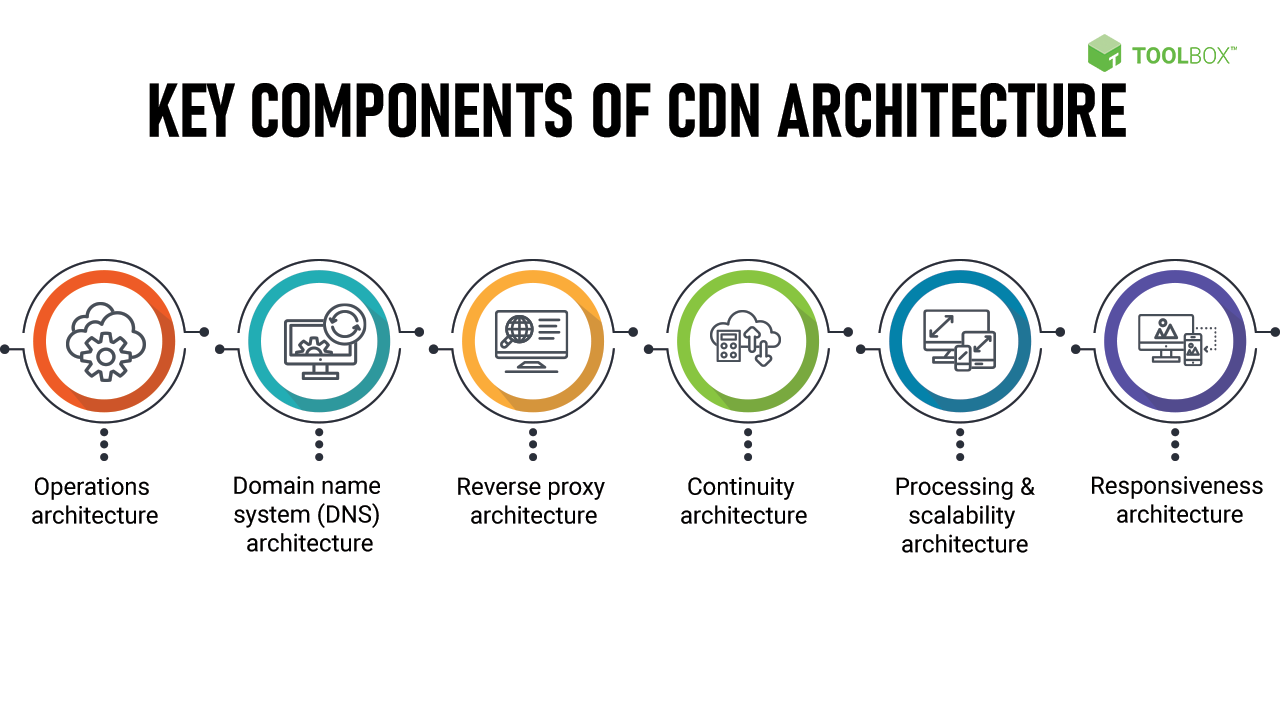
Key Components of VPC Architecture
In order to understand VPC architecture, it is essential to familiarize yourself with its key components. Let’s explore the main components that make up a VPC:
1. Subnets
A subnet is a range of IP addresses in a VPC. It represents a segmented portion of the VPC’s IP address range and can be associated with a specific availability zone. Subnets allow organizations to logically divide their VPC into smaller networks, enabling better resource management and network isolation.
Within a subnet, organizations can deploy resources such as virtual machines, databases, and load balancers. Each resource deployed within a subnet is assigned a private IP address from the subnet’s IP address range, allowing for seamless communication within the VPC.
Subnets can also be associated with network access control lists (ACLs) to control inbound and outbound traffic at the subnet level. By defining rules in the ACL, organizations can restrict or allow specific types of traffic, providing an additional layer of security.
2. Internet Gateway
An internet gateway is a horizontally scalable, highly available component that allows communication between instances in a VPC and the internet. It serves as the entry and exit point for traffic going in and out of the VPC.
By attaching an internet gateway to a VPC, organizations can enable instances within the VPC to access the internet and receive inbound traffic from the internet. This is particularly useful for instances that need to communicate with external services, download software updates, or serve content to users over the internet.
However, it’s important to note that the internet gateway does not provide any protection against unauthorized access. It is the responsibility of organizations to implement security measures, such as security groups and network access control lists, to secure their instances and data.
3. Route Tables
A route table is a set of rules that determine how traffic is directed within a VPC. It acts as a virtual router, directing traffic between subnets, internet gateways, virtual private gateways, and other connected networks.
Each subnet in a VPC must be associated with a route table. The route table contains entries that define the destinations of traffic and the target for routing. For example, a route table entry might specify that traffic destined for the internet should be directed to the internet gateway.
By configuring route tables, organizations can control the flow of traffic within their VPC, ensuring that it reaches the intended destinations. Route tables can also be used to establish connectivity between VPCs or on-premises networks using virtual private gateways or transit gateways.
4. Network Access Control Lists (ACLs)
Network Access Control Lists (ACLs) serve as a virtual firewall for subnets in a VPC. They allow organizations to control inbound and outbound traffic at the subnet level, providing an additional layer of security.
ACLs operate at the subnet level and evaluate inbound and outbound traffic based on a set of rules. These rules can permit or deny specific types of traffic, such as HTTP, HTTPS, or SSH. By configuring ACLs, organizations can restrict access to their resources and protect them from unauthorized access.
It’s important to note that ACLs are stateless, meaning that they do not keep track of the state of connections. Each packet is evaluated independently based on the rules defined in the ACL. This can sometimes lead to unexpected behavior, such as allowing outbound traffic but blocking the corresponding inbound traffic.
5. Security Groups
Security groups are another crucial component of VPC architecture that adds an extra layer of security to instances within a VPC. They act as virtual firewalls, controlling inbound and outbound traffic at the instance level.
Unlike network ACLs, security groups operate at the instance level and evaluate traffic based on a set of rules. These rules can permit or deny specific types of traffic, such as TCP, UDP, or ICMP. By configuring security groups, organizations can define fine-grained access control for their instances.
One of the key advantages of security groups is their stateful nature. They automatically allow inbound traffic that is a response to outbound traffic, simplifying the management of incoming and outgoing connections. This makes security groups an effective tool for controlling access to instances and protecting them from unauthorized access.
6. Elastic IP Addresses
Elastic IP addresses (EIPs) are static, public IPv4 addresses that can be associated with instances in a VPC. They allow instances to maintain a consistent public IP address even if they are stopped and started, providing a reliable endpoint for applications and services.
EIPs are particularly useful when instances need to communicate with external services or when organizations require a static IP address for specific use cases, such as hosting a website or running a mail server. By associating an EIP with an instance, organizations can ensure that it can always be reached at a predetermined IP address.
It’s important to note that there is a limit to the number of EIPs that can be associated with a VPC. Organizations should ensure that they only allocate the necessary number of EIPs to avoid unnecessary costs and resource usage.
7. Virtual Private Gateways
A virtual private gateway (VGW) is a virtual appliance that enables secure communication between a VPC and an organization’s on-premises network. It acts as a bridge between the VPC and the on-premises network, allowing traffic to flow securely between the two environments.
By establishing a VPN connection or a dedicated connection from the on-premises network to the virtual private gateway, organizations can extend their network into the VPC. This enables them to leverage the benefits of cloud computing while maintaining connectivity to their existing infrastructure.
Virtual private gateways provide a secure and reliable connectivity option for organizations that need to integrate their on-premises resources with their VPC. They ensure that traffic between the VPC and the on-premises network is encrypted and that the connection is highly available.
Understanding VPC Peering
VPC peering allows for seamless connectivity between VPCs, enabling efficient data transfer and resource sharing. In this section, we will delve into the intricacies of VPC peering, discussing its benefits, limitations, and best practices.
What is VPC Peering?
VPC peering is a networking connection between two VPCs that enables them to communicate with each other using private IP addresses. It allowsthe VPCs to act as if they are part of the same network, enabling direct and secure communication without the need for internet access or a virtual private gateway.
The Benefits of VPC Peering
VPC peering offers several benefits for organizations looking to establish connectivity between their VPCs:
1. Seamless Communication
With VPC peering, instances in different VPCs can communicate with each other using private IP addresses. This enables organizations to establish a seamless and secure network environment, allowing for efficient data transfer and resource sharing.
2. Cost Savings
By utilizing VPC peering, organizations can avoid the costs associated with data transfer between VPCs over the internet or through a virtual private gateway. Since the communication between VPCs is done through the internal network, there are no additional charges for data transfer.
3. Simplified Network Architecture
VPC peering simplifies the network architecture by eliminating the need for complex VPN configurations or dedicated connections. It allows organizations to create a flat network topology, making it easier to manage and monitor the connectivity between VPCs.
4. Increased Security
VPC peering enables secure communication between VPCs without the need for traffic to traverse the public internet. This enhances the overall security of the network environment, reducing the risk of unauthorized access or data breaches.
Limitations of VPC Peering
While VPC peering offers numerous benefits, there are some limitations to consider when implementing it:
1. Regional Availability
VPC peering is only available within the same AWS region. This means that VPCs in different regions cannot be directly peered. Organizations that require connectivity between VPCs in different regions will need to consider alternative solutions, such as transit gateways or inter-region VPC peering.
2. IP Address Range Overlap
When establishing a VPC peering connection, it is important to ensure that the IP address ranges of the VPCs do not overlap. Overlapping IP address ranges can cause routing conflicts and disrupt the communication between VPCs. Organizations should carefully plan their IP address ranges to avoid any conflicts.
3. Transitive Peering
VPC peering connections do not support transitive peering. This means that if VPC A is peered with VPC B and VPC B is peered with VPC C, VPC A and VPC C cannot directly communicate with each other. To enable communication between VPC A and VPC C, a separate VPC peering connection must be established between them.
Best Practices for VPC Peering
To ensure a successful implementation of VPC peering, organizations should follow these best practices:
1. Plan IP Address Ranges Carefully
Before creating VPCs and establishing peering connections, it is crucial to plan the IP address ranges carefully. This includes ensuring that the IP address ranges do not overlap and leaving room for future growth and scalability.
2. Enable DNS Resolution and DNS Hostnames
Enabling DNS resolution and DNS hostnames in the VPCs allows instances in the peered VPCs to communicate using their private DNS names. This simplifies the configuration and management of the network environment.
3. Implement Proper Security Measures
While VPC peering provides secure communication within the network, it is still important to implement proper security measures. This includes configuring network access control lists (ACLs) and security groups to control inbound and outbound traffic and regularly monitoring and auditing the network environment for any potential security risks.
4. Monitor and Troubleshoot Connectivity
Organizations should regularly monitor the connectivity between the peered VPCs to ensure that it is functioning as expected. This includes monitoring network traffic, checking for any routing issues, and troubleshooting connectivity problems in a timely manner.
Conclusion
VPC peering is a powerful feature of VPC architecture that enables seamless communication between VPCs, providing organizations with enhanced flexibility, cost savings, and increased security. By understanding the benefits, limitations, and best practices of VPC peering, organizations can effectively leverage this feature to create a well-connected and efficient network environment within their cloud infrastructure.
As you continue to explore the world of VPC architecture, remember to regularly review and update your network design to align with evolving business requirements and industry best practices. By embracing the capabilities of VPC peering and other VPC components, you can optimize your cloud infrastructure and unlock the full potential of cloud computing for your organization.