Understanding Server Architecture Diagram: A Comprehensive Guide
Welcome to our comprehensive guide on server architecture diagram. In this article, we will delve into the intricacies of server architecture, providing you with a detailed understanding of its components, importance, and how it impacts the performance of your website or application. Whether you are a tech enthusiast, a developer, or a business owner looking to optimize your server infrastructure, this article will equip you with the knowledge you need to make informed decisions.
What is Server Architecture?
Server architecture refers to the design and structure of a server infrastructure that facilitates the functioning of websites, applications, and other digital services. It involves the arrangement of various hardware and software components, as well as the establishment of connections and communication protocols between them.
At its core, server architecture enables the processing and delivery of data requests from clients to servers and vice versa. It ensures that the server infrastructure can handle multiple user requests simultaneously, optimizing performance, scalability, and security.
The Role of Server Architecture
The primary role of server architecture is to support the efficient functioning of websites and applications. It acts as the backbone of the digital infrastructure, providing the necessary resources and framework for data processing, storage, and transmission.
Server architecture determines how data flows within the system, ensuring that it reaches the intended recipients efficiently. It also plays a crucial role in load balancing, fault tolerance, and data security. By designing a robust server architecture, organizations can optimize their digital services, enhance user experience, and achieve business success.
Types of Server Architectures
There are various types of server architectures that organizations can choose from based on their specific needs and requirements. Let’s explore some of the most common ones:
Client-Server Architecture
The client-server architecture is the most prevalent type of server architecture in use today. It involves a central server that processes client requests and delivers the required data or services. Clients, such as web browsers or mobile applications, communicate with the server to retrieve information, submit requests, and receive responses.
The client-server architecture allows for centralized control, efficient resource allocation, and easier management of data and user access. It is widely used in web-based applications, email servers, and database management systems.
Peer-to-Peer Architecture
In contrast to the client-server architecture, peer-to-peer architecture distributes the processing and storage capabilities across multiple interconnected devices, known as peers. Each peer can act as both a client and a server, sharing resources and collaborating with other peers in the network.
Peer-to-peer architecture is commonly used in file-sharing applications, where users can directly download files from other users’ devices. It offers decentralized control, increased scalability, and improved fault tolerance. However, it can be more challenging to manage and secure compared to client-server architecture.
Cloud-based Architecture
Cloud-based architecture leverages the power of cloud computing platforms to host and deliver services over the internet. It involves the use of virtual servers, storage, and network resources provided by cloud service providers.
Cloud-based architecture offers scalability, flexibility, and cost-effectiveness, as organizations can easily scale their resources up or down based on demand. It eliminates the need for maintaining physical servers and allows for easy access to services from anywhere with an internet connection.
Importance of Server Architecture
Server architecture plays a crucial role in ensuring optimal performance, scalability, and security of websites and applications. Let’s explore the key reasons why server architecture is important:
Performance Optimization
A well-designed server architecture can significantly improve the performance of websites and applications. By strategically allocating resources, optimizing data processing, and minimizing latency, organizations can ensure that their digital services respond quickly and provide a seamless user experience.
Efficient load balancing techniques, such as distributing incoming requests across multiple servers, can prevent bottlenecks and ensure that the system can handle high traffic without compromising performance. Additionally, caching mechanisms can be implemented to store frequently accessed data, reducing the need for repetitive processing.
Scalability and Flexibility
Server architecture plays a crucial role in enabling scalability, allowing organizations to handle increasing traffic and accommodate growing user bases. Through techniques like horizontal scaling, where additional servers are added to distribute the load, organizations can ensure that their infrastructure can handle spikes in demand.
With cloud-based architectures, organizations can easily scale their resources up or down based on demand, avoiding the need for significant upfront investments in physical infrastructure. This flexibility allows businesses to adapt to changing needs and efficiently manage their resources.
Enhanced Security
Server architecture is closely tied to the security of digital services. By implementing robust security measures within the architecture, organizations can protect sensitive data, prevent unauthorized access, and mitigate the risk of cyber-attacks.
Firewalls, intrusion detection systems, and encryption techniques can be integrated into the server architecture to safeguard data and ensure compliance with industry regulations. Regular security audits and updates are also essential to address vulnerabilities and stay ahead of evolving security threats.
Components of Server Architecture
Server architecture consists of various components that work together to enable the smooth functioning of websites and applications. Let’s explore some of the key components:
Servers
Servers are the heart of the server architecture. They are powerful computers that host and process data, respond to client requests, and deliver the required services. Servers can be physical machines or virtual instances, depending on the chosen architecture.
Organizations can deploy multiple servers to distribute the workload and ensure high availability. Load balancing techniques, such as round-robin or least-connection, can be implemented to evenly distribute incoming requests across the server cluster.
Networking Equipment
Networking equipment, such as routers and switches, play a crucial role in server architecture. They enable the communication between servers, clients, and other network devices. Routers direct network traffic and establish connections between different networks, while switches facilitate communication within a network.
Organizations must carefully design their network infrastructure to ensure optimal performance, minimal latency, and high data transfer rates. Redundancy measures, such as using multiple routers or switches, can be implemented to minimize downtime and improve fault tolerance.
Storage Systems
Storage systems are responsible for storing and retrieving data within the server architecture. They can include hard disk drives (HDDs), solid-state drives (SSDs), or cloud-based storage solutions.
Depending on the requirements, organizations may opt for different storage configurations, such as RAID (Redundant Array of Independent Disks) setups for data redundancy or distributed storage systems for improved scalability.
Operating Systems
Operating systems serve as the foundation of the server architecture, providing the necessary software environment for running applications and managing hardware resources. Popular server operating systems include Linux distributions like Ubuntu, CentOS, or Red Hat Enterprise Linux, as well as Windows Server.
The choice of operating system depends on factors such as application compatibility, security considerations, and the expertise of the IT team. It is essential to keep the operating systems updated with the latest security patches and updates to mitigate vulnerabilities.
Web Servers
Web servers are responsible for processing and delivering web pages to clients in response to HTTP requests. They handle tasks such as interpreting and executing web scripts, managing user sessions, and handling database connections.
Popular web servers include Apache HTTP Server, Nginx, and Microsoft Internet Information Services (IIS). Web servers can be configured to support various programming languages and frameworks, such as PHP, Python, or Node.js, depending on the requirements of the application.
Database Systems
Database systems are crucial components of server architecture, responsible for storing and managing structured data. They provide efficient methods for data retrieval, insertion, deletion, and modification.
Popular database management systems include MySQL, PostgreSQL, Oracle Database, and MongoDB. Organizations must choose the appropriate database system based on factors like data volume, performance requirements, and scalability needs.
Designing an Effective Server Architecture
Designing an effective server architecture is crucial for ensuring optimal performance, scalability, and security. Let’s explore some key considerations and best practices:
Scalability and Redundancy
Scalability and redundancy are vital aspects of an effective server architecture. By designing a system that can handle increasing traffic and accommodate growing user bases, organizations can ensure that their infrastructure can scale seamlessly.
Horizontal scaling, where additional servers are added to distribute the load, is a common approach to achieve scalability. Redundancy measures, such as implementing backup servers or using RAID configurations for data redundancy, can improve fault tolerance and minimize downtime.
Load Balancing
Load balancing plays a crucial role in optimizing server architecture. By evenly distributing incoming requests across multiple servers, organizations can prevent bottlenecks and ensure that the workload is efficiently managed.
Load balancers can be hardware devices or software solutions that intelligently route traffic based on factors like server capacity, response times, or geographical proximity. Load balancing algorithms, such as round-robin, least-connection, or weighted distribution, can be employed to achieve optimal resource utilization.
Data Caching
Data caching can significantly improve server performance and reduce response times. By storing frequently accessed data in high-speedmemory or cache, organizations can minimize the need to retrieve data from slower storage systems, such as databases or file servers.
Cache mechanisms can be implemented at various levels, including the web server, application level, or even the client-side. Caching strategies, such as time-based expiration or cache invalidation based on data changes, can be employed to ensure that the cached data remains up-to-date.
Security Measures
Security is a critical aspect of server architecture. By implementing robust security measures, organizations can protect their infrastructure and data from unauthorized access, data breaches, and other security threats.
Firewalls and intrusion detection systems can be deployed to monitor network traffic and block malicious activities. Access control mechanisms, such as role-based access control (RBAC) or two-factor authentication, can be implemented to ensure that only authorized individuals can access sensitive resources.
Encryption techniques, such as SSL/TLS for securing data transmission or disk encryption for protecting stored data, can be employed to safeguard data confidentiality. Regular security audits, vulnerability assessments, and timely patching of software vulnerabilities are essential to maintain a secure server architecture.
Server Architecture Diagram Examples
To better understand server architecture, let’s explore some real-world examples of server architecture diagrams:
E-Commerce Server Architecture Diagram
In an e-commerce server architecture, the diagram typically includes components such as web servers, application servers, database servers, load balancers, and caching layers. The web servers handle incoming HTTP requests from clients, while the application servers process business logic and interact with the database servers.
Load balancers distribute incoming traffic across multiple web and application servers to ensure optimal resource utilization. Caching layers, such as Redis or Memcached, store frequently accessed data to improve response times. The database servers handle data storage and retrieval, ensuring the integrity and availability of transactional data.
Cloud-Based Server Architecture Diagram
In a cloud-based server architecture, the diagram typically includes components such as virtual servers, storage systems, load balancers, and networking infrastructure. Virtual servers, often hosted on cloud platforms like Amazon Web Services (AWS) or Microsoft Azure, provide the computational resources required to run applications.
Storage systems, such as AWS S3 or Azure Blob Storage, offer scalable and durable storage for data. Load balancers distribute incoming traffic across multiple virtual servers to ensure high availability and efficient resource utilization. The networking infrastructure, including routers, switches, and firewalls, facilitates communication between different components and ensures data security.
Server Architecture and Security
Server architecture and security go hand in hand. By integrating robust security measures into the server architecture, organizations can protect their infrastructure, data, and users from various security threats. Let’s explore some key aspects of server architecture and security:
Firewalls and Intrusion Detection Systems
Firewalls act as a barrier between the internal network and external networks, monitoring and filtering incoming and outgoing traffic based on predefined security rules. They help prevent unauthorized access, network attacks, and the spread of malware.
Intrusion detection systems (IDS) monitor network traffic and system logs for signs of malicious activities or policy violations. They generate alerts or take proactive measures to mitigate potential threats, such as blocking suspicious IP addresses or terminating suspicious connections.
Encryption and Secure Communication
Encryption is crucial for ensuring the confidentiality and integrity of data transmitted over networks or stored in storage systems. Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols can be implemented to establish encrypted communication channels between clients and servers.
Additionally, disk-level encryption can protect stored data, ensuring that even if physical storage media are compromised, the data remains inaccessible. Encryption algorithms, such as Advanced Encryption Standard (AES), provide strong encryption and are widely adopted in server architecture.
Access Control and Authentication
Access control mechanisms help prevent unauthorized access to server resources. Role-based access control (RBAC) can be implemented to grant permissions to users based on their roles or responsibilities within the organization.
Authentication mechanisms, such as username and password combinations, two-factor authentication, or biometric authentication, ensure that only authorized individuals can access sensitive resources. Strong password policies, regular password updates, and account lockout mechanisms can further enhance security.
Security Audits and Updates
Regular security audits and vulnerability assessments are essential to identify potential weaknesses in the server architecture. Penetration testing, code reviews, and security scanning tools can help uncover vulnerabilities and ensure that appropriate measures are taken to address them.
Keeping software and operating systems up to date with the latest security patches and updates is crucial for mitigating known vulnerabilities. Regular monitoring of security advisories and industry best practices is necessary to stay ahead of evolving security threats.
Scaling Server Architecture
Scaling server architecture is essential to handle increasing traffic and accommodate growing user bases. Let’s explore some strategies and techniques for scaling server architecture:
Horizontal Scaling
Horizontal scaling involves adding more servers to distribute the workload and handle increased traffic. By adding additional servers, organizations can achieve higher processing capacity, improved fault tolerance, and increased scalability.
Load balancers can be used to distribute incoming requests across multiple servers, ensuring that the workload is evenly distributed. This approach allows organizations to scale their infrastructure as demand grows, without relying on a single server to handle all traffic.
Vertical Scaling
Vertical scaling involves increasing the resources of existing servers, such as adding more RAM, CPU power, or storage capacity. This approach allows organizations to handle increased traffic and resource demands without adding additional servers.
Vertical scaling is often limited by the maximum capacity of the server hardware. However, it can be a cost-effective solution for organizations with specific resource requirements or limitations in adding more servers.
Cloud Computing and Auto Scaling
Cloud computing platforms, such as AWS or Azure, offer elastic scaling capabilities through features like auto scaling. Auto scaling automatically adjusts the number of server instances based on predefined performance metrics, such as CPU utilization or network traffic.
With auto scaling, organizations can scale their infrastructure up or down based on demand, ensuring optimal resource utilization and cost efficiency. Cloud-based architectures also provide additional benefits like pay-as-you-go pricing and easy provisioning of resources.
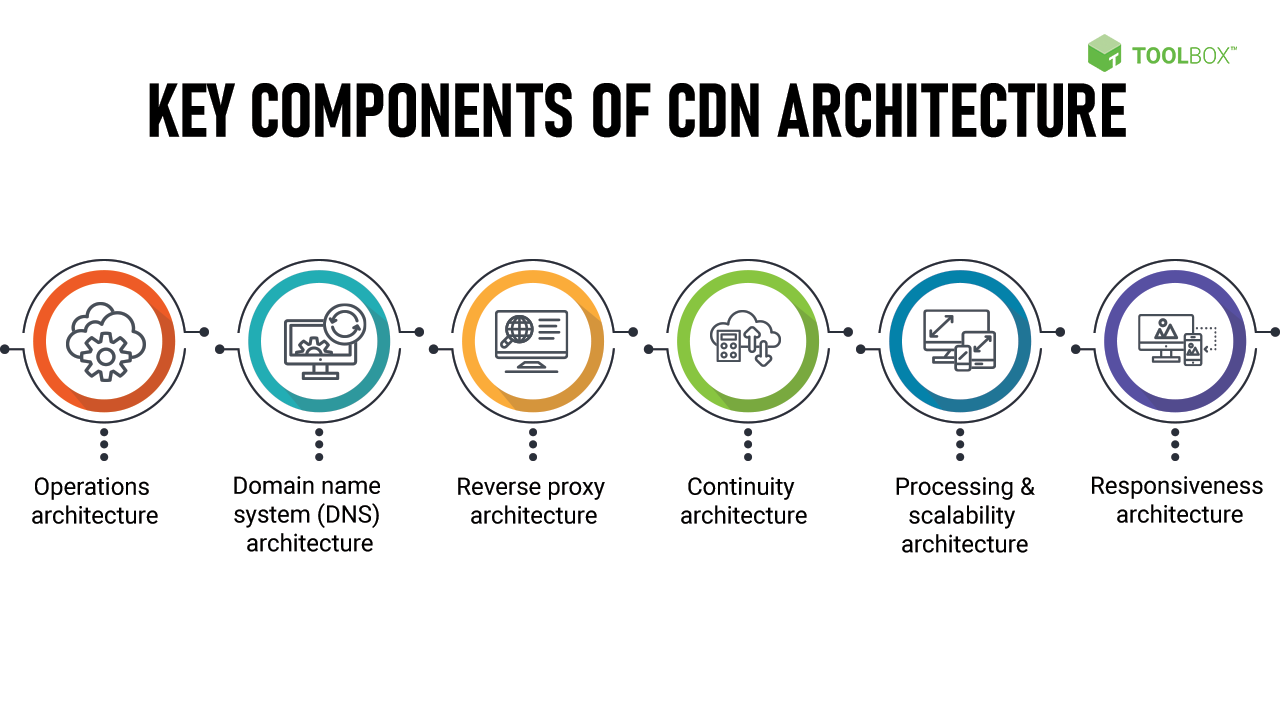
Content Delivery Networks (CDNs)
Content Delivery Networks (CDNs) can be employed to improve the performance and scalability of server architecture, particularly for websites or applications with a global user base. CDNs store cached copies of static content, such as images, JavaScript files, or CSS files, in edge servers distributed across multiple geographical locations.
When a user requests content, the CDN delivers it from the edge server closest to the user, minimizing latency and reducing the load on the origin server. CDNs can significantly improve the user experience by accelerating content delivery and reducing bandwidth consumption on the server infrastructure.
Common Server Architecture Challenges
Designing and managing server architecture can present various challenges. Let’s explore some common challenges and recommended solutions:
Scalability and Performance Bottlenecks
Managing scalability and performance can be challenging, especially when dealing with high traffic or resource-intensive applications. Inadequate resource allocation, inefficient load balancing, or poorly optimized code can lead to performance bottlenecks.
Regular performance testing, capacity planning, and monitoring can help identify potential bottlenecks and optimize the server architecture accordingly. Load testing tools and performance monitoring solutions can provide insights into system performance and identify areas for improvement.
Data Backup and Disaster Recovery
Ensuring data backup and disaster recovery is essential to protect against data loss and minimize downtime in the event of system failures or disasters. Organizations must have robust backup strategies in place, including frequent backups, offsite storage, and regular testing of backup restoration processes.
Implementing a disaster recovery plan that includes redundant systems, failover mechanisms, and backup power supplies can help minimize the impact of unexpected outages or disasters. Regular testing and updating of the disaster recovery plan are necessary to ensure its effectiveness.
Security and Data Privacy
Security and data privacy are ongoing concerns in server architecture. Organizations must stay updated with the latest security threats, vulnerabilities, and best practices to protect their infrastructure and data.
Regular security audits, vulnerability assessments, and penetration testing can help identify and address security weaknesses. Implementing encryption techniques, access control mechanisms, and security monitoring solutions can enhance the overall security posture of the server architecture.
Future Trends in Server Architecture
Server architecture continues to evolve as new technologies and trends emerge. Let’s explore some future trends that are shaping the future of server architecture:
Containerization and Microservices
Containerization, through technologies like Docker or Kubernetes, allows for efficient deployment and management of applications. Containers provide isolation, scalability, and portability, enabling organizations to easily package and deploy applications across different environments.
Microservices architecture complements containerization by breaking down applications into modular and independently deployable services. This approach allows organizations to develop, deploy, and scale individual services independently, enhancing flexibility and scalability.
Serverless Computing
Serverless computing, also known as Function as a Service (FaaS), abstracts the underlying server infrastructure, allowing developers to focus on writing and deploying functions or code snippets. With serverlesscomputing, organizations don’t need to provision or manage servers directly, as the cloud provider takes care of the infrastructure.
This approach offers benefits like automatic scaling, reduced operational overhead, and cost optimization, as organizations only pay for the actual execution time of their functions. Serverless computing is particularly useful for event-driven or sporadic workloads, where resources are only needed during specific events or periods.
Edge Computing
Edge computing brings computational capabilities closer to the source of data generation, reducing latency and improving real-time processing. By deploying servers or computing resources at the network edge, organizations can process and analyze data locally, without the need to transmit it to centralized data centers.
This trend is particularly relevant for applications that require low latency or deal with large amounts of data, such as Internet of Things (IoT) devices or real-time analytics. Edge computing can help organizations achieve faster response times, improved data privacy, and reduced network traffic.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are increasingly being integrated into server architecture to improve automation, efficiency, and decision-making capabilities. AI algorithms can analyze server data, identify patterns, and make predictions or recommendations for system optimization.
AI and ML techniques can be used for workload prediction and resource allocation, identifying potential performance bottlenecks, or detecting anomalies and security threats. By leveraging AI and ML, organizations can optimize server architecture and enhance overall system performance.
Conclusion
Server architecture is a critical component of any successful website or application. It determines the performance, scalability, and security of the infrastructure, directly impacting user experience and business success. By understanding the components, principles, and best practices of server architecture, organizations can make informed decisions and optimize their infrastructure for optimal performance.
From choosing the right type of server architecture to designing a scalable and secure system, each aspect plays a crucial role in achieving desired outcomes. Load balancing, caching, security measures, and scalability strategies are all integral parts of a well-designed server architecture.
As server architecture continues to evolve, embracing emerging trends like containerization, serverless computing, and edge computing can offer organizations new opportunities for efficiency, flexibility, and performance optimization.
By staying updated with the latest advancements, conducting regular audits, and adopting best practices, organizations can ensure that their server architecture remains robust, secure, and capable of meeting future demands. With a well-designed server architecture, businesses can provide seamless user experiences, achieve scalability, and stay competitive in today’s digital landscape.